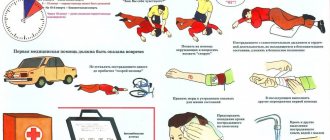
Subject Features
Every educational institution pays great attention to fire topics, and the task of parents is to promote such upbringing of the child at home. When making crafts, children gain certain labor skills and develop fine motor skills; they become familiar with fire safety rules and the difficulties of working in the Ministry of Emergency Situations.
Crafts can be taken to kindergarten or school, submitted to a competition, or simply used as a toy.
In the works on the topic under consideration, the following main plots stand out:
- What causes a fire and how dangerous it is. You can reflect the following directions: “Matches are not a toy”, “Be careful with fire”, “Do not light a fire in nature”, “From a spark begins a flame”, etc.
- Actions in case of fire. Of particular interest are fire extinguishing means and equipment. A bright fire truck is a popular craft. By making a fire shield, the child gets acquainted with the basic methods of fighting a fire.
Children's crafts can be created from different materials depending on the age and skills of the child. It is important to start with simple things, gradually moving on to more complex products.
Section "Regulatory and methodological support"
Here I would like to recall that a threat model can be developed for very different systems - from ISPD to CII. Therefore, the list of regulatory documentation may differ. For example, if we are developing a threat model for an automated process control system, then we need to remove FSTEC orders 21 and 17 from the template and add the 31st.
Documents marked with the abbreviation “CIPF” are regulatory documents of the FSB regulating the handling of encryption tools. If cryptocurrencies are not used in the information system (nowadays this is rare, but still), then these regulatory documents must be removed from the list.
A common mistake here is the addition of various GOSTs and other regulatory documents (they really like to include STR-K here), which are in no way related to threat modeling. Or canceled documents. For example, often in threat models you can find in the list of regulatory documents of the FSB the so-called “Methodological recommendations...” and “Standard requirements...”, which are no longer relevant.
Paper crafts
The simplest paper fire truck can be made using matchboxes:
- Its base is made up of 4 boxes, stacked in 2 rows in height.
- The fifth box is installed on top in the middle and imitates the cabin.
- All elements are glued together to form a rigid frame.
- Next, the workpiece is carefully covered with red paper on all sides.
- The windows are made of white paper, and yellow paper circles are glued as headlights.
- The fire escape is assembled from 2 parallel wooden branches (skewers) and transversely assembled matches. The ladder can be secured with plasticine.
- Wheels are taken from broken toy cars or cut out of cardboard.
With the help of adults, it is easy to make paper crafts using the papercraft technique. To do this you will need a thick sheet of paper. The turn of the car is drawn and painted on it. The photo shows a diagram of the headquarters fire truck. The workpiece is carefully cut out with scissors, and the parts are bent in the right places, glued together along the flaps, and the craft is ready.
You can also glue simple compositions from paper. A green background is created on a solid base (cardboard, plywood). A village house is made of paper. Windows and doors made of colored paper are drawn or glued on it, as well as flames escaping from the window. The craft is fixed to the base. A small fire truck is made in the same way.
Plasticine models
One of the first craft materials that a child gets acquainted with in early childhood is plasticine. You can make a beautiful fire truck out of it.
Master Class:
- Two large parts are formed from red plasticine - the base and the cabin, which are connected to each other.
- Windows made of thinly rolled white plates, yellow circles of headlights, a small blue signal light and a black bumper (a strip of black plasticine at the front bottom of the cab) are fixed to the cab.
- Thin strips and a number (01) made of white plasticine, as well as a fire hose coil in the form of a spiral made of gray plasticine flagellum, are installed on the base.
- The wheels are made of 2 parts: first, a disk is formed from black plasticine, a notch (tread) is applied to it along the perimeter, and a yellow circle is attached in the center.
- The ladder is made of gray material: cylinders with a diameter of 5-7 mm are formed and installed in parallel. Steps of the same color are attached to them.
Plasticine is a very malleable material. In addition to the car, you can make figures of firefighters out of it. A firefighting helicopter or airplane looks modern.
"FSB" sections
Next are the sections “Generalized capabilities of attack sources” and “Implementation of threats to information security, determined by the capabilities of attack sources.” These sections are not needed if crypto funds are not used. If they are still used, then the initial data, and in general tables for these sections, do not need to be invented; they are taken from the FSB regulatory document “Methodological recommendations for the development of regulatory legal acts that define threats to the security of personal data that are relevant when processing personal data in information personal data systems operated in the implementation of relevant types of activities" (approved by the management of the 8th Center of the FSB of Russia on March 31, 2015, No. 149/7/2/6-432).
It’s true that the result in our template is somewhat different from the default one given in the FSB document mentioned above.
The ultimate goal of these sections is to establish a class of cryptographic information protection tools (CIPF) that can be used in the system under consideration. This class directly depends on the capabilities of the offender and is established in accordance with FSB Order 378 (for personal data, but for other types of information there are simply no such requirements).
The most commonly used class of crypto funds is KS3. Now we'll tell you why.
In general, in the document “Composition and content of organizational and technical measures to ensure the security of personal data during their processing in personal data information systems using cryptographic information protection tools necessary to fulfill the requirements established by the Government of the Russian Federation for the protection of personal data for each level of security” ( approved by Order No. 378 of the FSB of Russia dated July 10, 2014), the CIPF class for the system in question is established, firstly, based on the type of threats, and secondly, based on the capabilities of the intruder.
We won’t go into detail about the types of threats; there is a lot of information on the Internet. Let’s dwell on the fact that there are 3 types of threats and by hook or by crook, if we plan to use cryptography, we need to deal with the 3rd type of threats (irrelevant threats associated with undeclared capabilities in application and system-wide software). Why?
Because FSB order 378:
- CIPF class KA in cases where type 1 threats are relevant to the information system;
- CIPF class KV and higher in cases where type 2 threats are relevant to the information system;
- CIPF class KS1 and higher in cases where type 3 threats are relevant to the information system.
It seems clear, but what is the problem? The problem is that you cannot buy CIPF classes KA1, KV1 and KV2 just like that, even if you have a lot of money for what they cost.
Let's do a little "investigation". Download the latest CIPF register, look for CIPF class KA1. The first search that came up was “Hardware-software encoder M-543K.” We go to Google, write “Buy M-543K hardware-software encoder” - failure. We try to “buy” the next crypto-tool – again a failure. We simply type in “buy crypto-tool KA1” - failure. We only receive links to other crypto tools of classes KS1-KS3 or to forums where cryptography is discussed. But the fact is that, as has already been said, you cannot simply buy CIPF of the KA and KV classes, only through specialized military units. Why these cryptocurrencies were mentioned at all in the document on personal data is still not clear. Therefore, in a regular ISPD there is only the third type of threat.
We sorted out KA and KV, but why KS3 and not KS2 and KS1? Here the second condition is already to blame - the violator.
FSB order 378:
12. CIPF class KS3 is used to neutralize attacks, when creating methods, preparing and carrying out which, the capabilities listed in paragraphs 10 and 11 of this document and at least one of the following additional capabilities are used:
a) physical access to electronic devices on which CIPF is implemented and SF; b) the ability to have hardware components of CIPF and SF, limited by measures implemented in the information system in which CIPF is used, and aimed at preventing and suppressing unauthorized actions.
Here the logic is like this:
- such common CIPF as, for example, ViPNet Client or CryptoPRO CSP are implemented on user workstations;
- users are potential violators;
- a potential violator has physical access to the computer equipment on which their CIPF and operating environment are implemented.
Thus, we can justify a lower class of CIPF only by justifying that our users are not potential violators (difficult), or by using only crypto gateways that are located in server rooms, to which, in turn, only privileged users, whom we have excluded, have access from the list of potential violators.
Applications
One of the most common trends in fire themes is applications. A simple craft in the shape of a fire truck is made from colored paper. The photo shows a cutting diagram. The outline of the parts is drawn on paper and cut out. On a thick sheet of paper on which the desired color background is created, the largest parts are first glued, and then the small ones are attached to them.
It is more difficult to make a composition. The photo shows a firefighter fighting a fire. His figurine can be cut out from a magazine or printed on a color printer, assembled from a certain number of parts cut out of colored paper. Lines and very small details are drawn with a felt-tip pen.
Introduction to the Threat Model
Okay, let's move on to the contents of the document.
I think about the title page, the list of abbreviations, terms and definitions, everything is clear. Although, perhaps, it’s worth taking a closer look at... suddenly the title page.
In the template, it is signed by the manager of the owner of the information system. It's not just like that.
Decree of the Government of the Russian Federation of May 11, 2021. No. 555:
4. The terms of reference for the creation of the system and the model of threats to information security are approved by an official of the executive authority who is entrusted with the appropriate powers.
Naturally, if the information system is not state-owned and the system operator is not an executive authority, then anyone can sign the threat model. It’s just that we have encountered more than once when, when the above conditions were met (state information system of an executive authority), the customer asked us to change the title page so that there were signatures only of representatives of the licensee company (that is, ours). We had to explain why FSTEC would return such a threat model for revision.
Drawings
Crafts in the form of drawings require certain skills, but in kindergarten one should not strive for artistic performance, the main thing is that children feel the importance of their work.
The photo shows an example of how a child sees the process of extinguishing a fire in a house using fire equipment. Of course, parents should help as much as possible in choosing a plot, then the best drawings can be submitted to the competition.
Children's creativity uses colored pencils, felt-tip pens, and wax crayons. Gradually mastering watercolor and gouache.
Another direction is drawings by adults for children. They must reflect basic fire safety rules. The photo shows how you can attract children's attention to the phone number to call in case of a fire.
Creative approach to learning
Unfortunately, not all kids will listen to you if you just lecture them. Uninteresting information quickly disappears from their heads. Therefore, you need to take it using other methods.
And one of these methods is creating crafts with your own hands on the topic of fire safety, road safety, water safety, and more. This will obviously attract a lot more attention and force them to absorb at least some useful knowledge.
Crafts from cereals
Quite simple crafts can be created from semolina. To do this, colored semolina is prepared: the cereal is mixed in a container with gouache of the desired color until a rich shade is obtained and dried. For a fire truck you will need red, black and gray semolina, as well as undyed (white) semolina.
The outline of the machine is drawn on a sheet of thick paper or cardboard. Glue is applied inside the lines and red material is poured in a thin, even layer, and excess grain is shaken off. Then other colors are carefully formed into small details. When the picture is ready, glue is applied to the paper outside the outline, creating a general background of unpainted semolina.
Vulnerabilities
As we remember, the threat model must indicate possible vulnerabilities. This section is not yet included in the downloadable threat model template, so we will briefly describe how to deal with it.
The compiler of a threat model should immediately have a question: should a list of vulnerabilities identified by the scanner be attached to the document? The question is good and the answer is not clear-cut. We know colleagues who do exactly this, but we think this approach is wrong and here’s why.
Firstly, the information security threat model is a document, although subject to change, but still more or less static. Developed once and forgotten until significant infrastructure changes in the system.
The list of vulnerabilities generated by scanners is very dynamic information. Today we identified vulnerabilities, tomorrow we fixed them and scanned them again - we received a new report. The day after tomorrow new signatures appeared, the scanner was updated and found new vulnerabilities, and so on in a circle. What is the point of attaching a vulnerability scanner report made at the time the threat model was developed? None.
Secondly, a threat model can be created for an information system that does not yet physically exist (designed but not built). In this case, we can’t even scan anything.
The way out of this situation is simple.
Indicate in the threat model not specific vulnerabilities indicating the CVE identifier and CVSS rating, but list possible classes of vulnerabilities for a specific information system. And to give this list some credibility, let’s take this list not from our heads, but from GOST R 56546-2015 “Information Protection. Vulnerabilities of information systems. Classification of information system vulnerabilities." The list is under the spoiler. We take it and remove the unnecessary ones that are not compatible with the structural and functional characteristics of our system. The section is ready! Vulnerability classes according to GOST
Vulnerabilities by area of origin:
- code vulnerabilities;
- configuration vulnerabilities;
- organizational vulnerabilities;
- multifactorial vulnerabilities.
Vulnerabilities by type of information system deficiencies:
- vulnerabilities associated with incorrect configuration of software parameters;
- vulnerabilities associated with incomplete verification of input data;
- vulnerabilities associated with the ability to follow links;
- vulnerabilities associated with the possibility of OS command injection;
- vulnerabilities associated with cross-site scripting (script execution);
- vulnerabilities associated with the injection of arbitrary code;
- memory buffer overflow vulnerabilities;
- vulnerabilities associated with deficiencies leading to leakage/disclosure of restricted information;
- vulnerabilities related to credential management;
- vulnerabilities related to permissions, privileges and access management;
- authentication vulnerabilities;
- vulnerabilities associated with cryptographic transformations;
- cross-site request forgery vulnerabilities;
- vulnerabilities related to resource management.
Vulnerabilities by place of occurrence (manifestation):
- vulnerabilities in system-wide (general) software;
- vulnerabilities in application software;
- vulnerabilities in special software;
- vulnerabilities in technical means;
- vulnerabilities in portable hardware;
- vulnerabilities in network (communications, telecommunications) equipment;
- vulnerabilities in information security measures.
More complex crafts
As you gain certain skills, you can move on to more complex crafts. Already at school age, interest in other technologies appears. Attention is paid to quality of execution, volume and layout.
Volume projects
Volumetric crafts are created in different ways:
- Volumetric figure. An example would be a campfire, a common cause of fire. Logs (cylinders of thick paper) are laid out on a sheet of cardboard; a bunch of “flames” cut out from colored paper in red, yellow and orange are collected in the center.
- Three-dimensional pictures are made in the form of a double-leaf postcard made of thick paper. On the inside of one of the halves, various figures are glued to the bent edge: an image of a fire, trees, which are pressed by the second flap, but when it is turned away, they take a vertical position. On the second half, a drawing or appliqué is made. When positioned vertically, it creates the main background of the picture.
Complex crafts are available for older children. The photo shows the three-dimensional composition “Fire Extinguishing”. In it, each element is made in different ways. For example, in the photo the fire truck is made of Lego, the firefighters are made of plasticine, and the burning house is made of wood rods laid in the form of a log house.
Why do we need a threat model?
The need to develop a threat model is regulated by a number of regulatory documents. Here are some of them.
Part 2 of Article 19 of Law No. 152-FZ “On Personal Data”:
2. Ensuring the security of personal data is achieved, in particular:
1) identifying security threatspersonal data when processed in personal data information systems;
The composition and content of organizational and technical measures to ensure the security of personal data during their processing in personal data information systems (approved by order of the FSTEC of Russia dated February 18, 2013 No. 21):
4. Measures to ensure the security of personal data are implemented, including through the use of information security tools in the information system that have passed the conformity assessment procedure in accordance with the established procedure, in cases where the use of such tools is necessary to neutralize current threats to the security
of personal data.
Requirements for the protection of information that does not constitute a state secret contained in state information systems (approved by the FSTEC of Russia dated February 11, 2013 No. 17)
Formation of information security requirements... including: ... identification of information security threats
, the implementation of which may lead to a violation of information security in the information system, and the development of an information security threat model based on them; ...
Requirements for ensuring the protection of information in automated control systems for production and technological processes at critically important facilities, potentially hazardous facilities, as well as facilities that pose an increased danger to human life and health and to the environment (approved by order of the FSTEC of Russia dated March 14, 2014 No. 31):
Formation of requirements for information protection in an automated control system... including: ... identification of threats to information security, the implementation of which may lead to disruption of the normal functioning of the automated control system, and development
on their basis
of a model of threats to information security
;
Requirements for ensuring the security of significant objects of critical information infrastructure of the Russian Federation (approved by order of the FSTEC of Russia dated December 25, 2021 No. 239):
11. The development of organizational and technical measures to ensure the security of a significant object is carried out by the subject of the critical information infrastructure... and should include:
a) analysis of threats to information security and development of a model of threats to information security or its clarification (if any);
So, the conclusion from here is simple: for any information systems that are somehow subject to protection in accordance with the law, it is necessary to develop a threat model.
Dough crafts
Salt dough successfully replaces plasticine. It is also malleable, but when hardened it becomes hard and can retain its shape for a long time. This blank can be painted and varnished. Dough recipe:
- For 200 mg of flour add 150 mg of table salt and 5 tbsp. vegetable oil.
- The components are diluted with water to the desired consistency.
From the prepared plastic mass you can easily fashion a fire truck and a helicopter, houses engulfed in flames, emergency workers, etc. The workpiece is placed in the oven and dried at a temperature of +70...+80 0C for 1 hour. Accelerated drying is provided at a temperature of +110...+120 0C for 25-30 minutes. After cooling, the hardened workpiece can be painted in any color using acrylic paints.
Trimming
Unusual crafts are obtained using the trimming technique. Essentially, this is a mosaic laid out from paper elements that will have a cone shape. To do this, small squares are cut from corrugated (crepe) paper and rolled into a cone. Using trimming you can make spectacular volumetric applications and entire panels. Glue is applied to a dense base and the conical elements are carefully installed one by one. They are pressed using wooden sticks, toothpicks or knitting needles.
Fabric crafts
Applications using colored patches look very impressive. Such paintings have an important advantage: they can be made soft using thick fabric as a base. The photo shows a warning picture that will remind you of the dangers of matches. The necessary details are sewn onto the woven base. To add volume, cotton wool is placed under some flaps. Human figures or his face can be embroidered or drawn.
Another direction is voluminous woven crafts. In the photo there is a “Fun Fire Extinguisher”. You can use foam rubber or polystyrene as a base. The base is covered with red fabric. Characteristic small details are sewn on. They can be made from ribbons, braid, felt. This craft is absolutely safe for kids.
Description of the information system
Here general information about the information system is indicated - where it is located, what it is called, what data and what class (security level, category) are processed. Here, of course, many are interested in how much detail an information system needs to be described.
In the process of repeated coordination of threat models for government information systems, we have developed a solution regarding this - there must be a golden mean. This should not be a copy-paste from a technical passport indicating the serial numbers of technical equipment. But on the other hand, a person who is not familiar with the system, who has read its description in the threat model, should roughly understand how this very system works.
Example:
The server part of the Nipel information system is a cluster of physical servers on which the ESXi 6.x hypervisor is deployed.
The operation of the server part of the main services of the information system is provided by virtual servers (server names) running operating systems (list of OS). The main software that implements technological processing processes is (software name). The application software is a client-server application. The client part runs as a thick client on user workstations running operating systems (list of operating systems). Users gain access to the information system both from a local network and via the Internet using secure communication channels. In general, the information system functions as shown in the diagram. A functional (not topological!) diagram of the information system is attached.
This is roughly what it usually looks like. Style and other details, of course, can vary greatly, the main thing is the information that can be gleaned from the description.
There is also a section “Premises Security”. Here we describe how the premises are protected during working hours and during non-working hours - video surveillance, access control system, security guard, watchman, alarm system and that's all.
The purely FSB sections “Determining the relevance of using CIPF to ensure the security of personal data” and “Additional protection objects” are also included here in the threat model template. If cryptography is not used, then we simply remove these sections; if it is used, then, in general, there is no need to change anything special there, except to enter the name of the information system.
The “Threat Model Principles” section also does not need to be changed. Just note that there is an option for when the system uses crypto and when it doesn't. We select the one we need and move on.
Crafts from napkins
Paper napkins make magnificent crafts. One popular option is to roll napkins into small balls and soak them in gouache of different colors. From such elements you can put together a three-dimensional picture. The technology is the same as when working with beads.
Even a small master can make voluminous figures from such lumps. The photo shows a small composition on a fire theme. The frame of a machine or structure is assembled from matchboxes or cardboard boxes. On top it is tightly covered with balls of napkins, painted in the desired color.
Crafts reflecting fire-fighting themes, made by a child together with an adult, help to learn the basic rules of fighting fire. They can be made from different materials and in different ways. It is important to inspire the little master to be creative, and he will receive the necessary information during the process of work.
Contents of the threat model
We’ve sorted out the need to create a document, let’s see what the legislation prescribes for us in terms of its content. Here, oddly enough, everything is quite sparse.
As a textbook example of describing the content of a threat model, we can cite FSTEC Order 17:
The model of threats to information security must contain a description of the information system and its structural and functional characteristics, as well as a description of threats to information security, including a description of the capabilities of violators (intruder model), possible vulnerabilities of the information system, ways to implement threats to information security and the consequences of violating information security properties.
You won't believe it, but that's all. But on the other hand, although there is not a lot of text, it is quite informative. Let's re-read and write down what should be in our threat model:
- description of the information system;
- structural and functional characteristics;
- description of security threats;
- intruder model;
- possible vulnerabilities;
- ways to implement threats;
- consequences of violation of information security properties.
This is according to the law, which is required by FSTEC. There are also additional requirements of the FSB (more on them a little later) and some informal requirements and wishes from the FSTEC, which we encountered in the process of agreeing on threat models for government information systems.